IGA Guide: Setting up Tide E2EE
This developer-focused guide walks you through configuring and using Tide's data encryption and decryption features via realm roles and OIDC clients.
Prerequisites
Before you begin, ensure that:
- You have admin access to the TideCloak Admin Console
- TideCloak is upgraded to the latest version
- You have a realm with:
- Tide IDP added and licensed
- IGA enabled and your admin account granted the
tide-realm-adminrole
To set up IGA, see Setup IGA
Process Overview
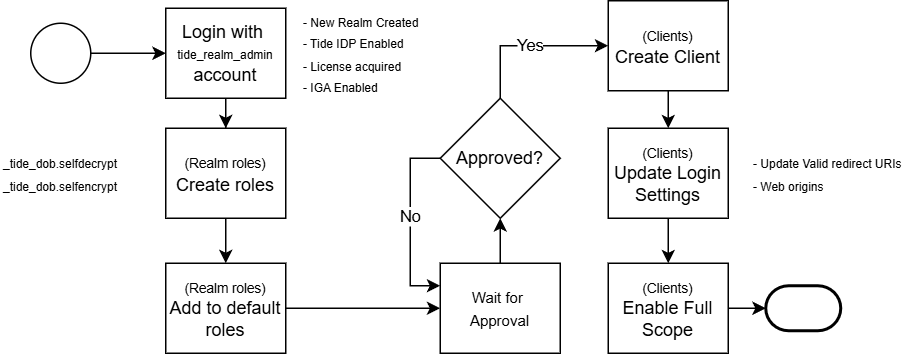
1. Define Encryption/Decryption Roles
Tide uses realm-level roles to gate encrypt/decrypt operations on specific data fields.
-
Open the Admin Console → Realm roles → Create role.
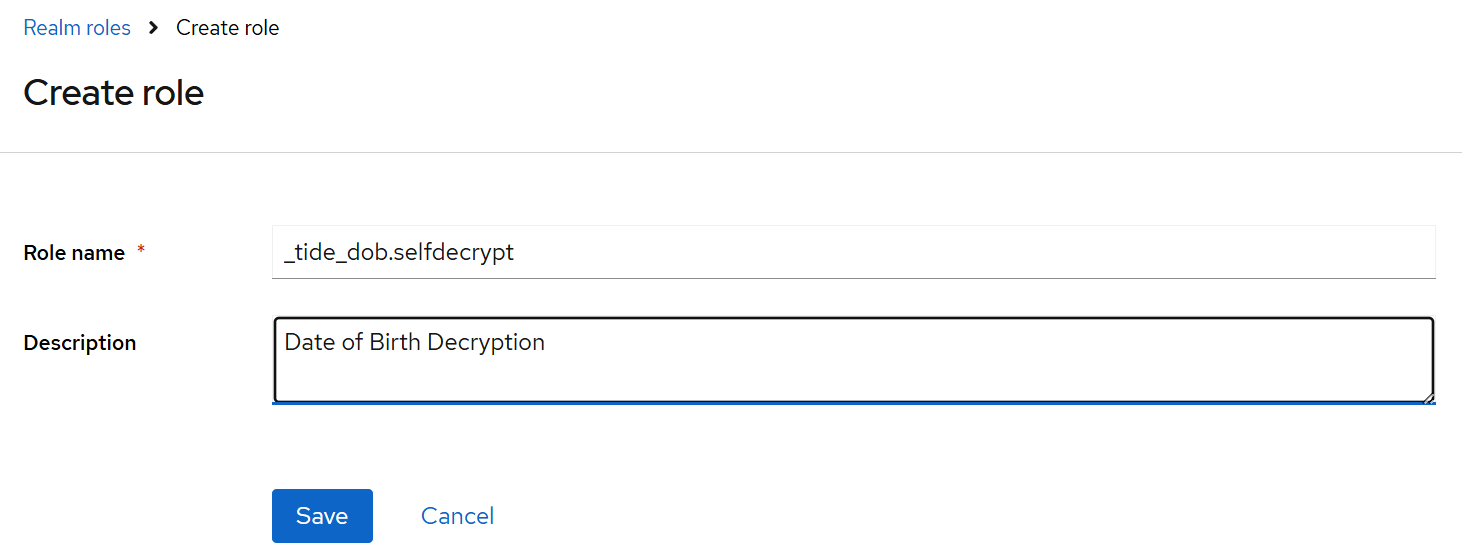
-
Create two roles for each field you wish to protect. For example, to protect
dateOfBirth:_tide_dob.selfencrypt
_tide_dob.selfdecrypt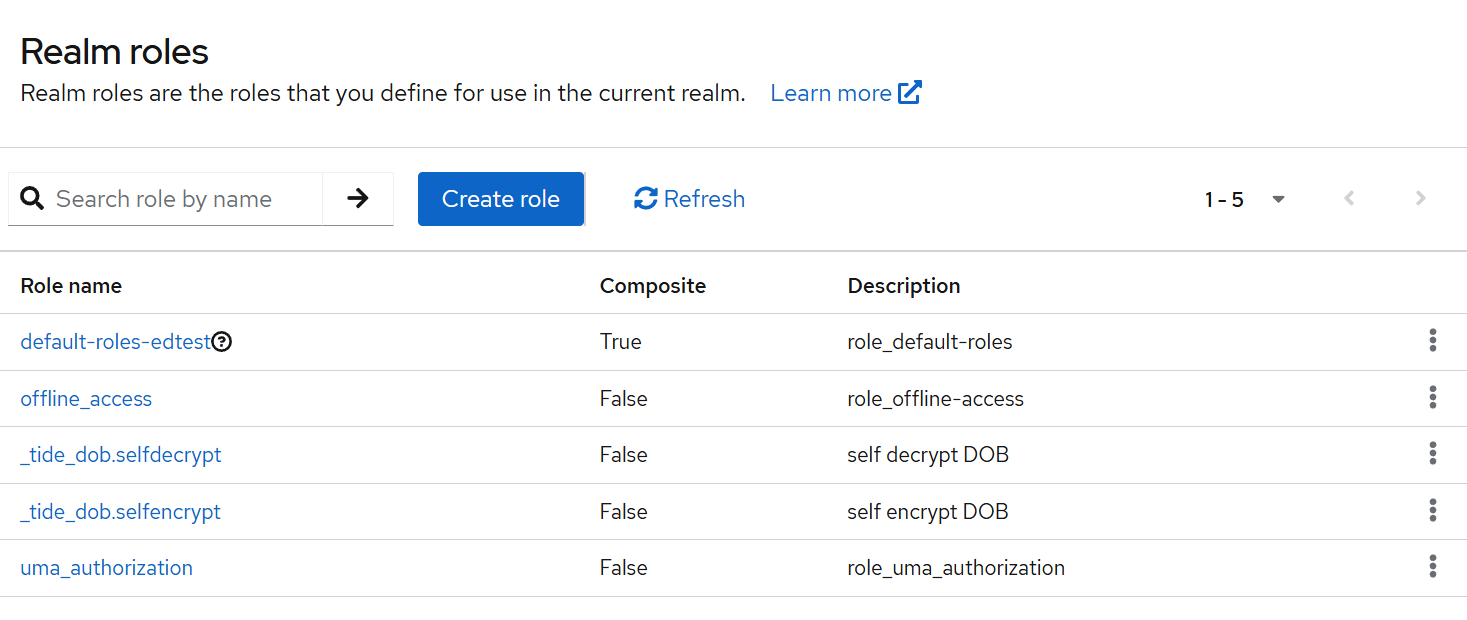
-
Assign these roles to your user defaults group (
default-roles-edtest):
-
In Realm roles, select
default-roles-edtest -
Click Assign role → filter for your new roles → Add
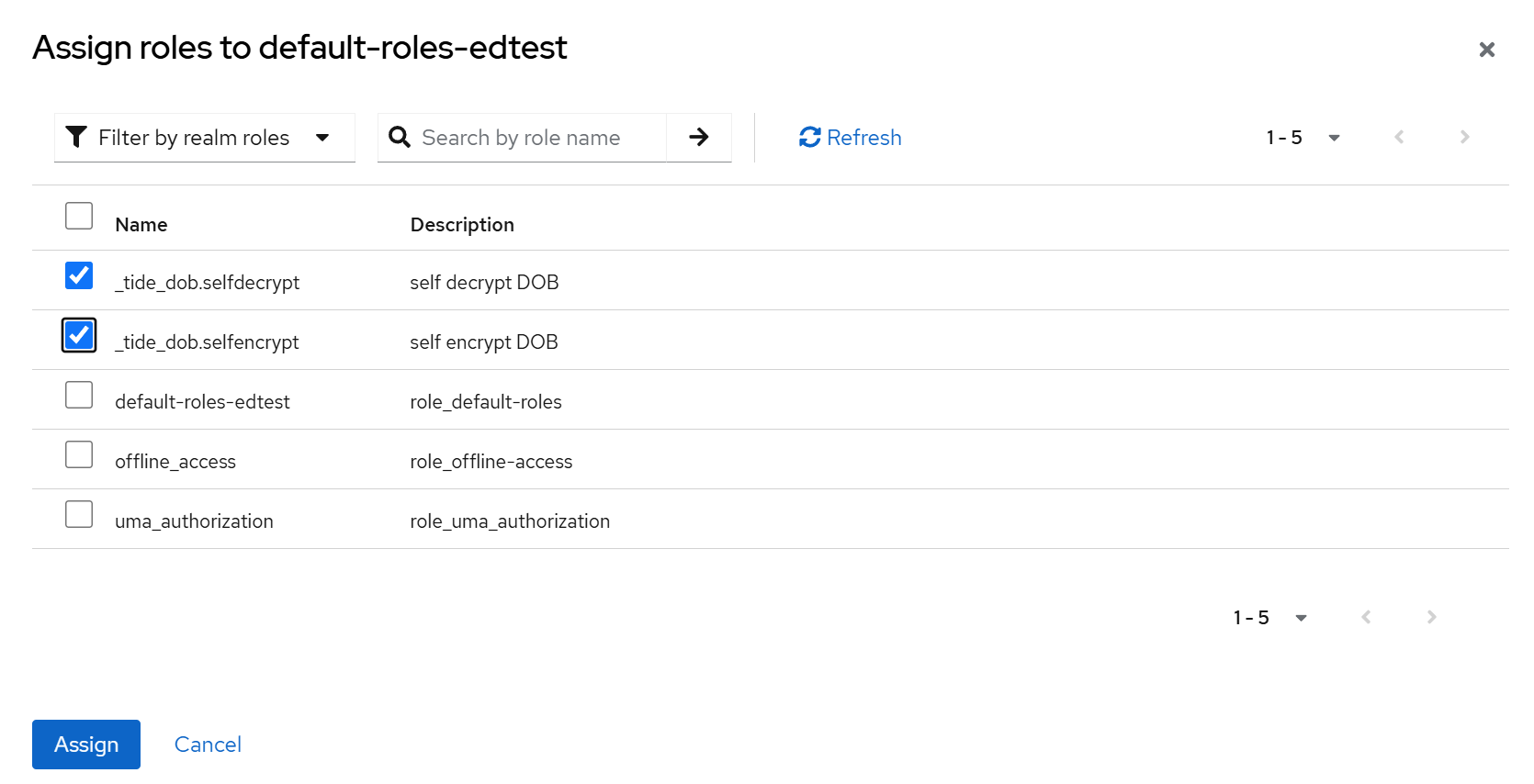
-
Approve the role assignment via your Change Management workflow
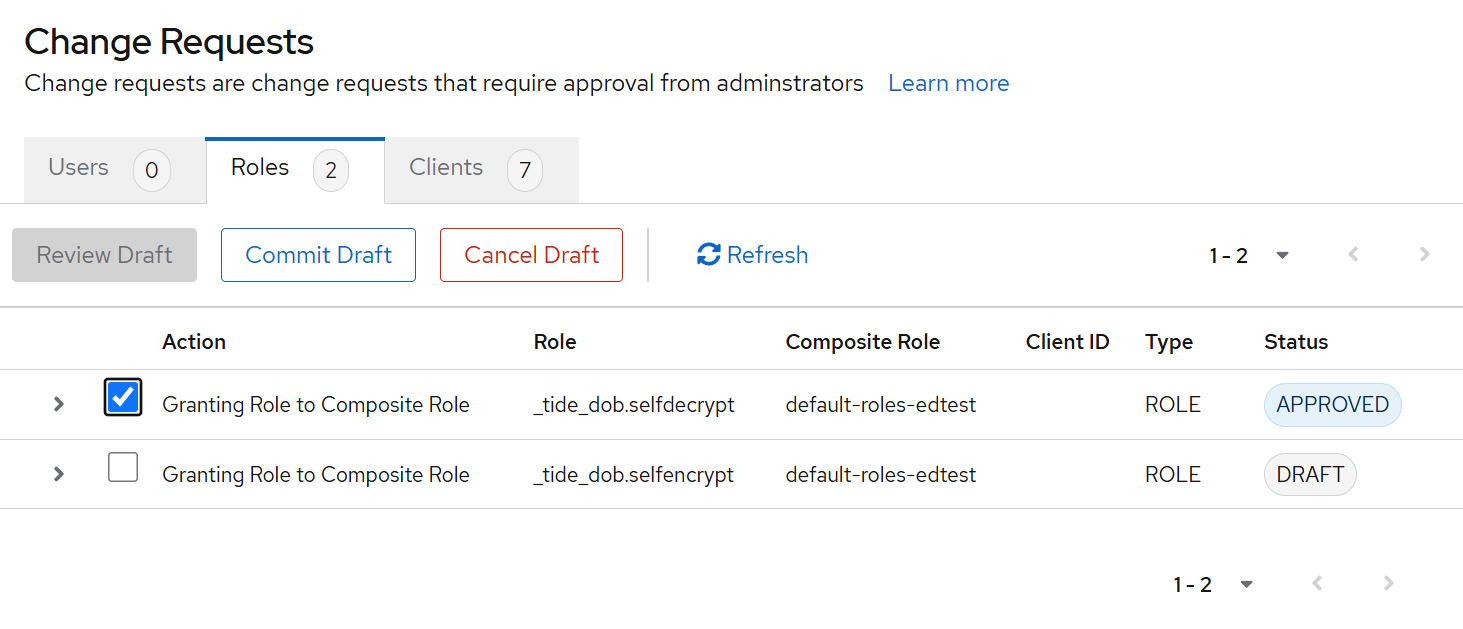
-
After approval, you should see both roles listed under
default-roles-edtest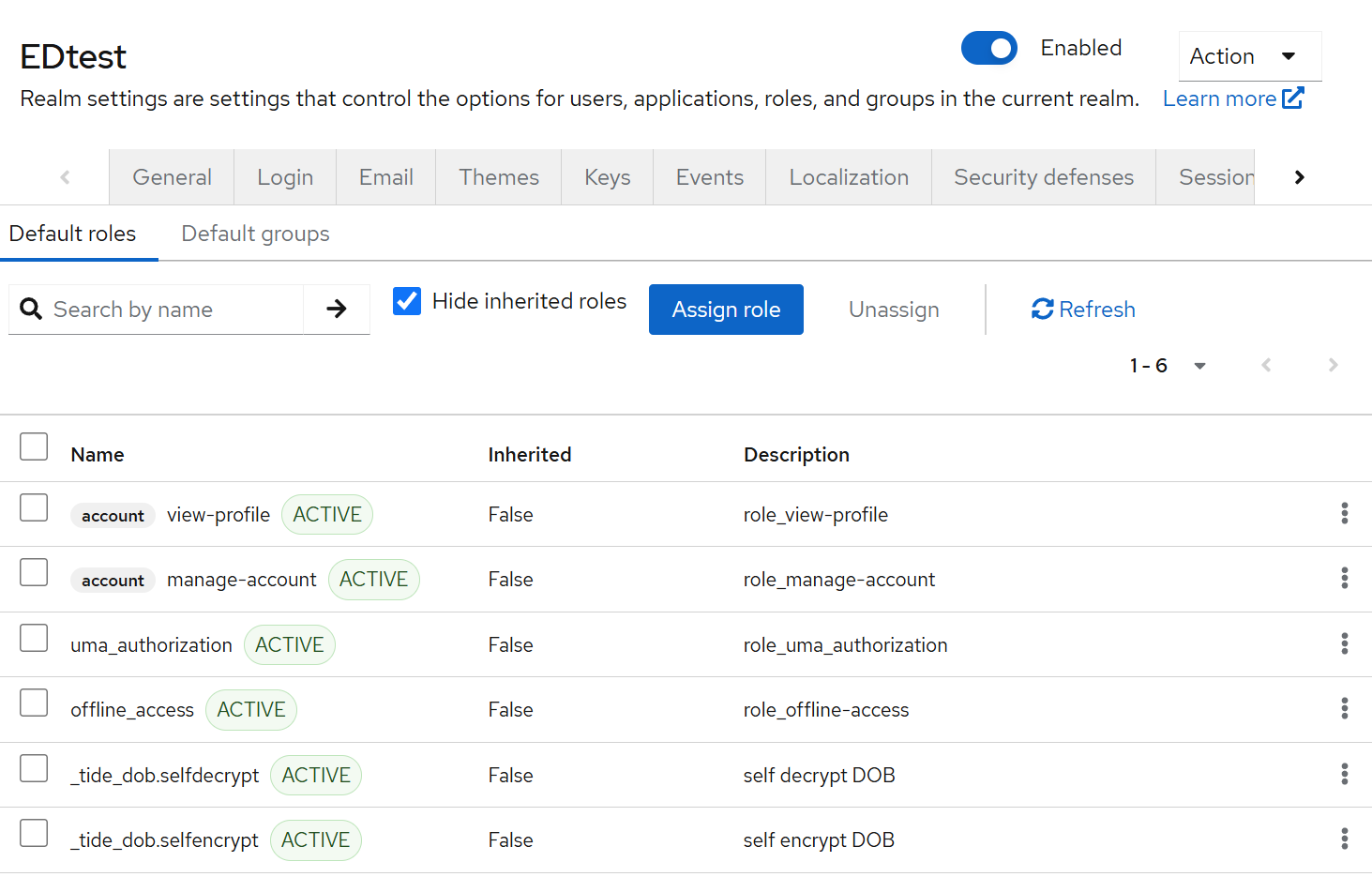
2. Create an OIDC Client
Your application must authenticate with Tide and request the appropriate scopes for encryption/decryption.
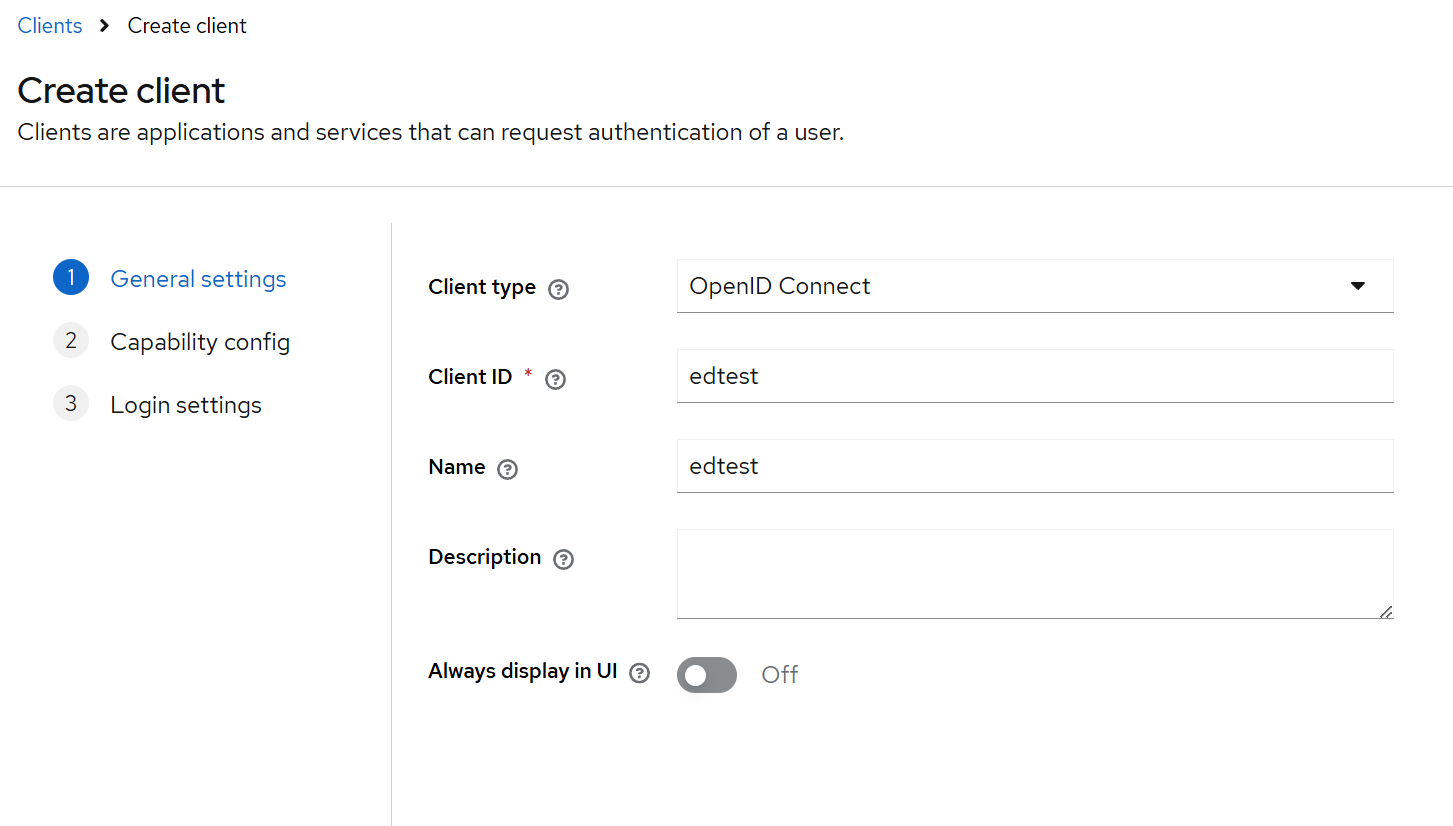
- Navigate to Clients → Create client:
-
Client type: OpenID Connect
-
Client ID: e.g.
edtest-client -
Name: descriptive label
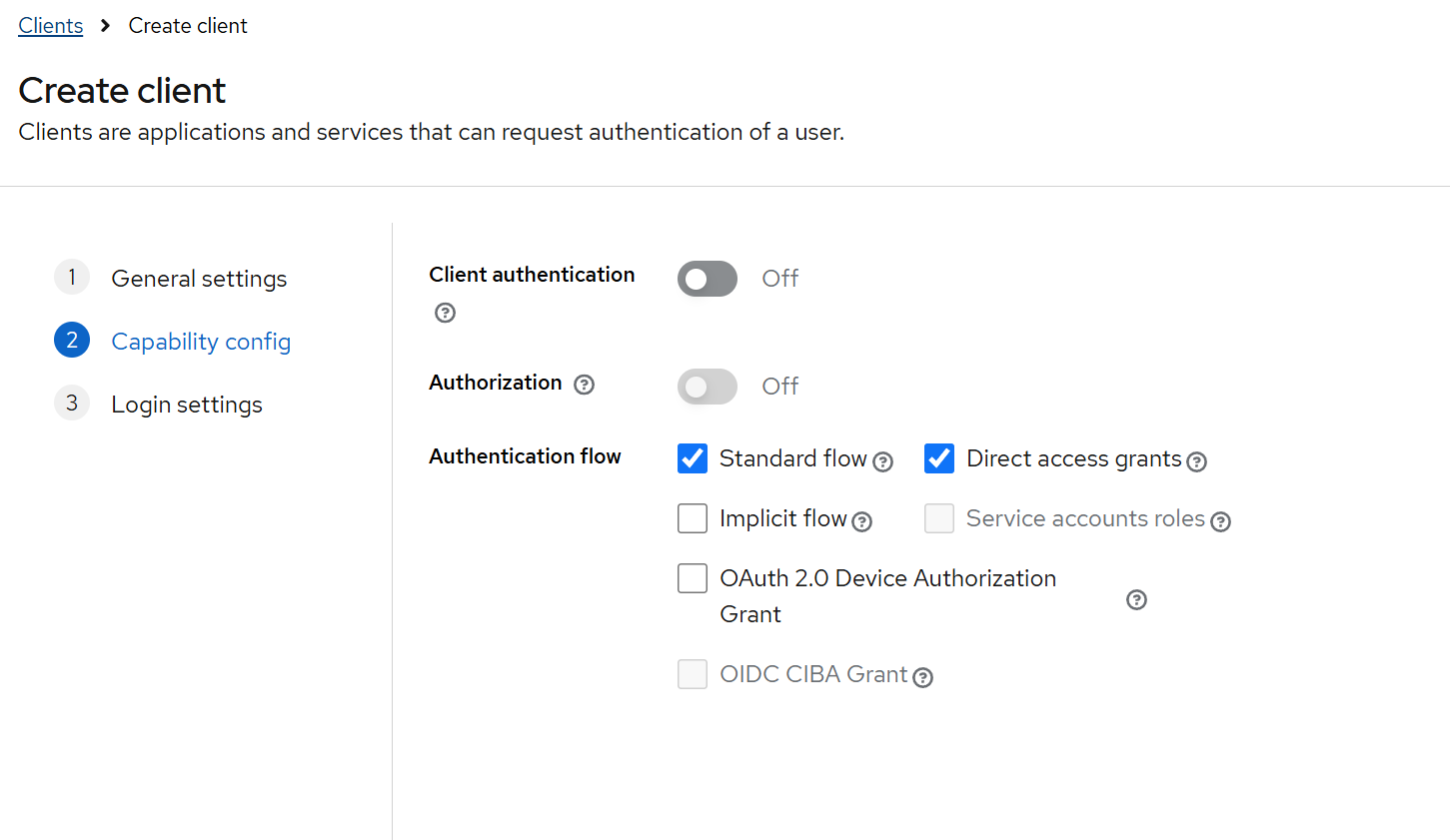
-
Configure redirect URIs, web origins, and enable Full scope allowed. For example, in a Next.js sample client:
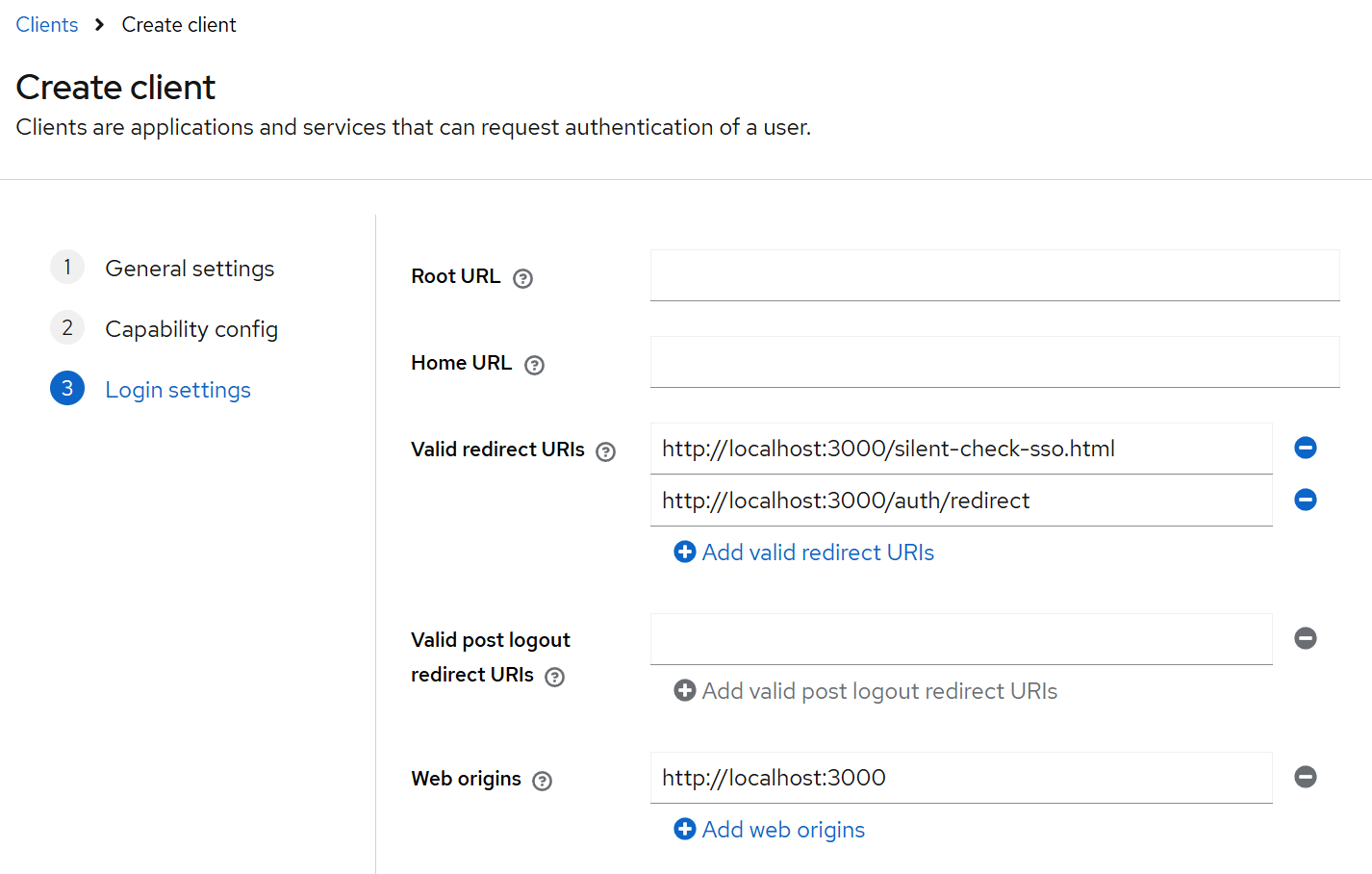
-
Enable scopes:
- Go to the Client Scopes tab
- Select your client (e.g.
edtest-dedicated) - Under Scopes, toggle Full scope allowed
3. Encrypt & Decrypt via API
Once roles and client are in place:
- Acquire tokens: Request an OIDC token with the
openidand any custom scopes (e.g._tide_dob.selfencrypt) - Call Encrypt endpoint:
POST /realms/<realm>/protocol/openid-connect/encrypt
Authorization: Bearer <access_token>
Content-Type: application/json
{
"field": "dateOfBirth",
"value": "1980-01-01"
}
The response returns ciphertext.
- Call Decrypt endpoint:
POST /realms/<realm>/protocol/openid-connect/decrypt
Authorization: Bearer <access_token>
Content-Type: application/json
{
"field": "dateOfBirth",
"ciphertext": "<returned_ciphertext>"
}
The response returns the original plaintext.
Next Steps
- Integrate these calls into your backend or SDK.