TideCloak Authorization Flow
TideCloak implements an enhanced OAuth 2.0 Authorization Code Flow designed for secure server-side applications. It adds decentralized key management and a novel trust model to improve security, privacy, and user control.
At a high level, this flow:
- Redirects the user to TideCloak's Authorization Server for login.
- Exchanges the resulting authorization code for access and ID tokens.
- Authorizes access using decentralized credentials and session-based permissions.
Decentralized Key Management
TideCloak replaces centralized secrets with a sharded key infrastructure powered by Secure Multiparty Computation (SMPC).
- The user's Consumer Master Key (CMK) is never fully constructed or stored.
- Instead, the CMK is split into encrypted shards across independent nodes in the Tide network.
- When a cryptographic operation is required (e.g., signing, decryption, verification), each node performs a partial computation on its shard.
- SMPC protocols securely combine these partial results to complete the operation - without ever reassembling the full key.
Why it matters
- Eliminates single points of failure and key leakage risks.
- Makes insider attacks and centralized breaches infeasible.
- Guarantees that no party - not even TideCloak - can access a user's full key at any point.
Decentralized Authentication
TideCloak replaces centralized identity providers with decentralized cryptographic proofs:
- Users authenticate using double-blind authority credentials based on PRISM.
- Validation is performed via the CMK shards and SMPC across the network.
- No single authority or service ever has full visibility into the user's identity or credentials.
Developer Note
During the authorization request, you'll receive a verifiable credential token usable across compliant Tide nodes. No central ID service is required to validate user claims.
Distributed Authority
After successful authentication:
- The user receives a session key scoped to a specific set of permissions.
- This key is cryptographically bound to the decentralized identity.
- Authority is validated using the same SMPC-based process across the Tide node network.
Implementation Tip
Your backend should verify session key signatures and scopes by consulting any TideCloak node, which coordinates validation via distributed consensus.
User Ownership
With TideCloak, users have cryptographic ownership of their identity and credentials:
- The CMK remains under the user's control and is never exposed, stored, or reconstructed.
- All sensitive operations are executed through distributed SMPC protocols across the network.
- Access to user-bound resources requires multi-node consensus - not central server permission.
TL;DR for Developers
If you're building with TideCloak:
- No secrets to store - all keys are distributed and handled via SMPC.
- Authenticate using verifiable, decentralized credentials.
- Authorize actions using session keys backed by cryptographic proofs.
- Respect user-owned identity - the system ensures that no full key ever exists in one place.
TideCloak Authorization Code Flow: Step-by-Step Breakdown
The following diagram outlines the full OAuth 2.0 Authorization Code Flow as implemented by TideCloak, augmented with decentralized key management and cryptographic authority enforcement.
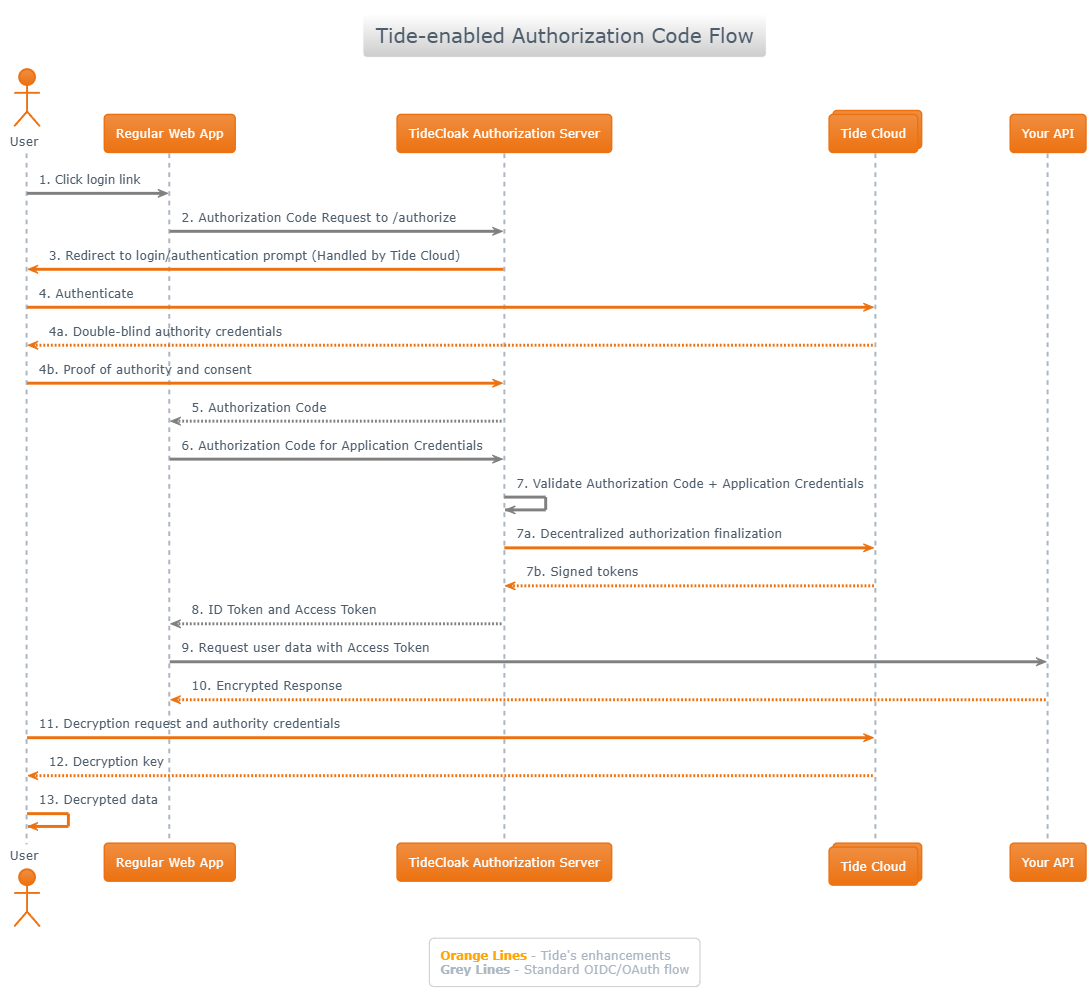
Detailed Flow Steps
- User Initiates Login
- A user clicks a login link in your app.
- Your frontend redirects to
/authorizeto start the OAuth flow.
- /authorize Request Sent
- The app sends a standard OAuth request to the TideCloak Authorization Server.
- TideCloak enhancement: This endpoint is distributed - requests are handled by a decentralized mesh of nodes in the Tide Network.
- Redirect to Authentication UI
- The user is redirected to the TideCloak-hosted login screen.
- This interface is served from the decentralized Tide network.
- User Authenticates
- The user enters credentials.
- 4a. Decentralized Proof of Identity: TideCloak uses the user's CMK (sharded) and PRISM to issue double-blind authority credentials.
- 4b. Session Key Created: Upon consent, a session key is issued and bound to the authenticated identity.
- Authorization Code Issued
- After successful authentication and consent, the user is redirected back to the app with an authorization code.
- Code Exchange for Tokens
- The app sends the authorization code and client credentials to TideCloak's
/tokenendpoint. - TideCloak enhancement: Instead of reconstructing the CMK, each node performs a partial cryptographic operation using SMPC.
- Token Issuance & Decentralized Validation
- 7a. Code Validation: The Tide nodes validate the code and credentials via consensus.
- 7b. Token Generation: Access and ID tokens (JWT) are signed using decentralized key signing logic - no single node ever holds the full key.
- Tokens Received by App
- The app receives the ID Token and Access Token to authenticate and authorize requests.
- Access Protected Resource
- The app uses the Access Token to call your protected API endpoints.
- Encrypted Data Response
- The resource server returns encrypted user data.
- Decryption Request + Proof of Authority
- The app or user client submits a request to decrypt data.
- Session key proof is submitted as authorization.
- Re-encryption applied to scope the decrypted content to the requesting user context.
- Decryption Key Issued
- After successful validation, TideCloak issues a decryption key via SMPC - assembled cryptographically, without reconstructing any private material.
- Data Decrypted
- The user or client decrypts the data locally.
- At this point, the secure, authenticated flow is complete and access is granted.
When to Use TideCloak's Authorization Flow
Use this flow if you're building a:
- Server-side web or backend service that requires secure session-based authorization.
- System that demands high-assurance user authentication and fine-grained access control.
- Platform where zero-trust principles or decentralized identity is a requirement.
- Solution needing data privacy, cryptographic proof of access, and resilience against single-point failure.
TideCloak's decentralized enhancements provide strong guarantees of integrity, non-repudiation, and ownership, making it ideal for sensitive applications like finance, identity management, healthcare, or decentralized platforms.