Authorization Flow with TideCloak
The Authorization Code Flow is a widely used OAuth 2.0 flow, primarily designed for server-side applications where the server can securely store a client secret. This flow involves the application directing the user to the Authorization Server to obtain an authorization code, which is then exchanged for tokens that grant access to protected resources.
TideCloak enhances this flow by incorporating decentralized key management , providing additional layers of authentication , authority , and ownership throughout the process.
What is Decentralized Key Management?
TideCloak's decentralized key management system is a core feature that enhances both security and privacy by distributing the user's cryptographic keys across multiple nodes in the network. Unlike traditional systems where a single entity controls the key management process, TideCloak fragments the user's Consumer Master Key (CMK) into multiple shards, each stored on a different node. This approach ensures that no single node or entity ever has access to the entire key. When needed, these shards are combined through secure cryptographic protocols to recreate the key for authorization purposes, but the key never resides in a complete form in any one place. This not only protects against unauthorized access but also mitigates the risk of a single point of failure, making the entire system more robust and resilient to attacks. By decentralizing key management, TideCloak empowers users with true control over their identity and data, ensuring that access to their resources can only be granted through a decentralized consensus of multiple parties, further reducing the risks associated with centralized key storage and control.
Authentication:
In the traditional flow, a user's authentication is handled by a central authority. However, with TideCloak, the user's identity is authenticated in a decentralized manner using a double-blind authority Credentials . This method leverages PRISM and the user's Consumer Master Key (CMK) , ensuring that the authentication is both secure and private, with no single entity having full control over the process. This guarantees that the user's identity can be verified without compromising sensitive information.
Authority:
TideCloak assigns authority through the use of session keys . When the user authenticates, they receive a session key that grants them access to perform specific actions within the system. This session key is validated across the Tide network to ensure its legitimacy. Additionally, the authority to access specific data or resources is tied to this decentralized key management system, making the entire authorization process more secure and tamper-proof. This reduces the risk of breaches caused by centralized control.
Ownership:
In traditional OAuth flows, ownership of data and identity is typically managed by a central server. With TideCloak, ownership is distributed across the Tide network. The user retains control over their own private key (CMK) , which is fragmented and stored in shards across multiple nodes. This decentralization ensures that no single node has access to the user's full key, and therefore no single entity can claim full ownership of the user's data or credentials. The user truly owns and controls access to their information, which can only be unlocked by their proof of authority, making the system significantly more resilient to attacks or breaches.
Overview of the Flow
In the Authorization Code Flow with TideCloak, the steps below explain how the process works, including the specific modifications introduced by TideCloak to enhance security through decentralized key management.
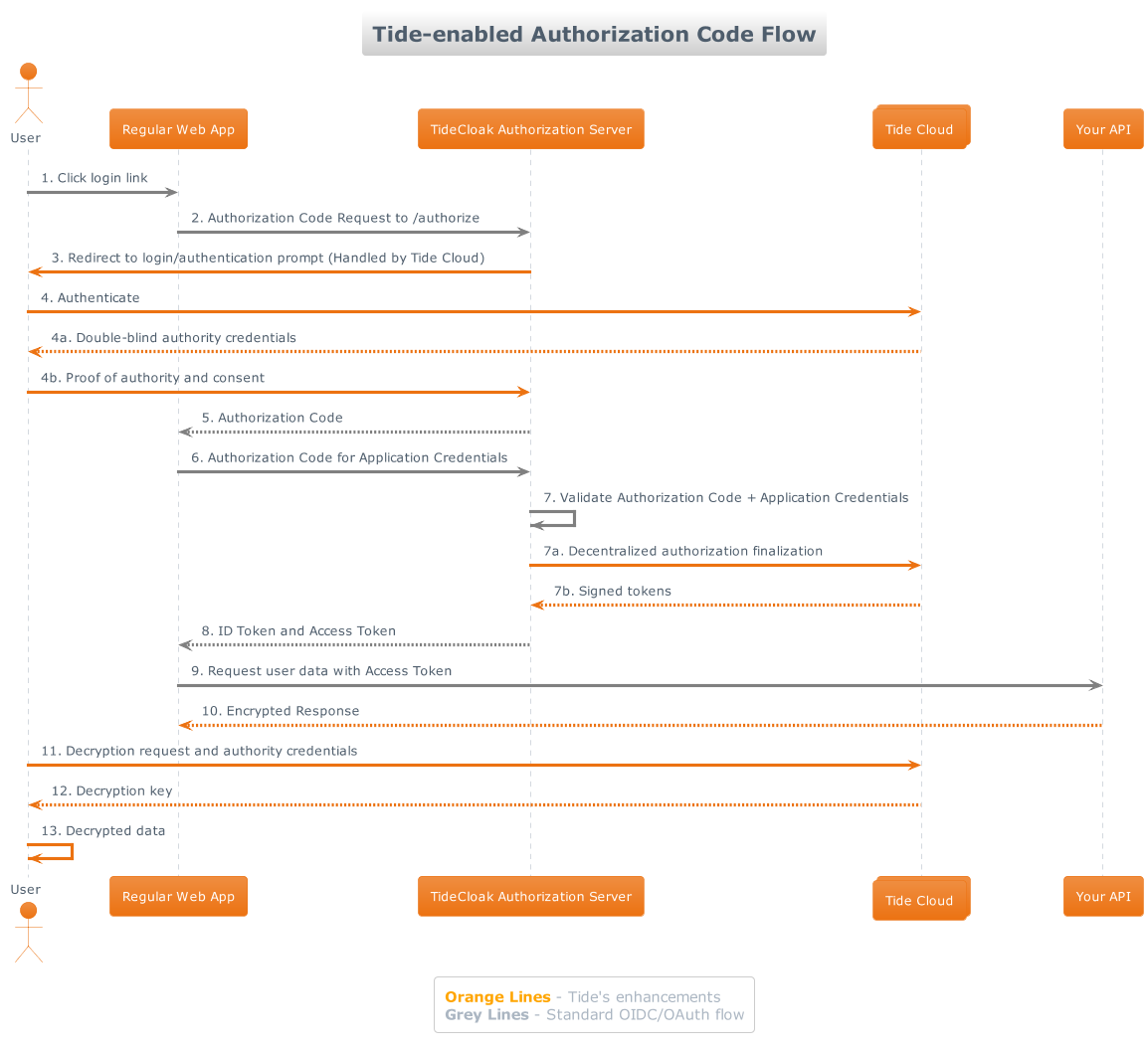
Step-by-Step Explanation:
- User Clicks Login Link The user starts the login process by clicking a link in the web app. This triggers the OAuth flow.
- Authorization Code Request to /authorize The app requests an authorization code from the TideCloak Authorization Server. TideCloak Modification: This request is handled in a decentralized manner across multiple nodes in the Tide Cloud.
- Redirect to Login/Authentication Prompt The user is redirected to the TideCloak Authorization Server to authenticate, which is managed by the decentralized Tide Cloud.
- Authenticate The user provides credentials. 4a. Double-blind Authority Credentials (PRISM and CMK): Tide uses PRISM and the user's CMK to handle the proof of identity and authority using blind signatures, while a session key is established. 4b. Authority Credentials and consent: The user confirms their identity and consent using the session key.
- Authorization Code The TideCloak Authorization Server issues an authorization code to the app after successful authentication.
- Authorization Code for Application Credentials The app exchanges the authorization code for tokens. TideCloak Modification: The user's key is securely reconstructed across decentralized nodes to validate the exchange.
- Validate Authorization Code + Application Credentials TideCloak verifies the authorization code and app credentials. 7a. Decentralized authorization finalization: Final validation occurs via the Tide Cloud's decentralized network. 7b. Signed tokens (JWT): Tide generates and signs the JWT, ensuring token security.
- ID Token and Access Token The app receives the ID Token and Access Token to access protected resources.
- Request User Data with Access Token The app uses the Access Token to request user data from the API.
- Encrypted Response The API responds with encrypted data.
- Decryption request and proof of authority The user requests decryption by proving authority, using the same session key from step 4. Re-encryption: Data is decrypted, and re-encryption ensures secure access by the authorized user.
- Decryption key The user receives the decryption key from Tide Cloud after validation.
- Decrypted data The user decrypts the data and can now access it within the application.
When to Use the Authorization Code Flow with TideCloak
This flow is recommended for server-side applications where the security of the tokens and the integrity of the authorization process are paramount. The addition of TideCloak's decentralized key management makes it particularly suitable for applications requiring enhanced security measures.